SecPoint® Premier Cyber Security Solutions
Next-Generation Firewall
Vulnerability Scanning
WiFi Penetration Testing
Committed to Privacy: No data collection.
The SecPoint Penetrator also offers white-labeling and Managed
Featured products
-
SecPoint Penetrator S9 - Security Software Vulnerability Assessment
Regular price From $219.00 USDRegular priceUnit price per -
SecPoint Protector P9 - Enterprise Virtual Appliance
Regular price From $529.00 USDRegular priceUnit price per -
SecPoint Portable Penetrator - WiFi Penetration Testing Security Software
Regular price From $99.00 USDRegular priceUnit price per -
SecPoint Cloud Penetrator S9 - Website Security Scanner - SQL Injection
Regular price From $79.00 USDRegular priceUnit price per -
SecPoint Penetrator S9 - 8 IP Concurrent Scan License Vuln Scanning (1U Rack Mountable )
Regular price From $2,499.00 USDRegular priceUnit price per -
SecPoint Penetrator S9 - 4 IP Concurrent Scan License Vuln Scanning SFF 1Y
Regular price From $1,699.00 USDRegular priceUnit price per -
SecPoint Protector P9 - 10User UTM Firewall (1 Year License) 1U Rack Mountable
Regular price From $2,499.00 USDRegular priceUnit price per -
SecPoint Protector P9 - 10 User UTM Firewall (1 Year License) Small Form Factor (SFF)
Regular price From $1,699.00 USDRegular priceUnit price per
Best Cyber security Products in the following Categories
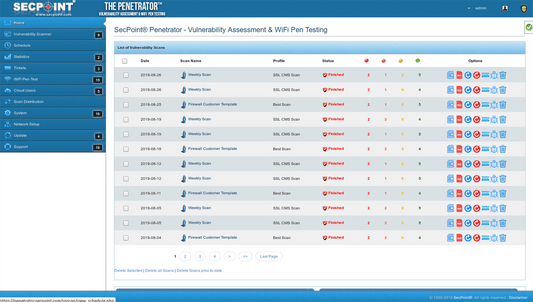
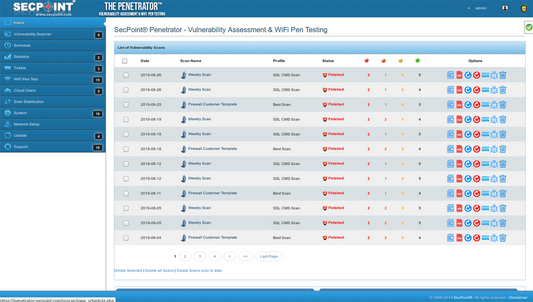
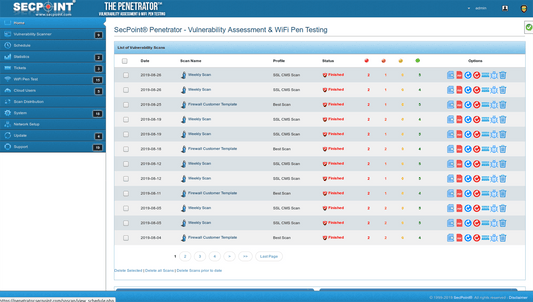
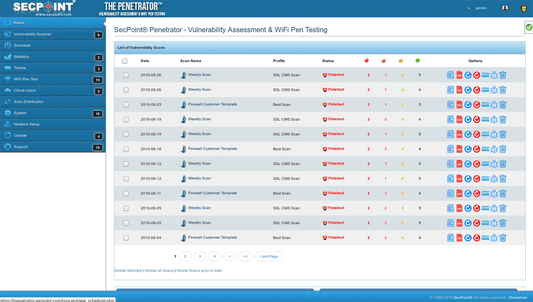
SecPoint® Penetrator™ - Vulnerability Scanning / Assessment Software
 Low Entry Cost from 219$ - 199 Euro
Low Entry Cost from 219$ - 199 Euro
 No Data Collection Full Privacy
No Data Collection Full Privacy
 Advanced AI most Accurate scans
Advanced AI most Accurate scans
 Whitelabeling, Report rebranding, logo, name
Whitelabeling, Report rebranding, logo, name
 19 scanning profiles
19 scanning profiles
- Virtual or Hardware Appliance Vulnerability Scanner
- 17 Language support in the reporting Profiles
- Professional PDF reporting for Consultant, Technical & Executive.
- Schedule Automatic Scanning
- Managed Service Provider (MSP) Multi User Support.
SecPoint® Penetrator™ Virtual Appliance Click here
SecPoint® Penetrator™ 1U Appliance Click here
Concurrent IP License explained:Example with the software Penetrator if you have a 8 IP license and you put in 256 IPs.
Then it will queue the 256 IPs and scan concurrent 8 at a time until it finish the queue.
You can scan any local or public IPs.
And you can the next day put 512 IPs to scan and it is same principle it will queue the IPs then do 8 IPs at a time.
You are only limited by concurrent scans but you can do all the scans you want and change the IPs as much as you want.
SecPoint® Protector™ - UTM Firewall High Speed 64 Bit UTM Firewall VPN
 UTM Firewall & Web Filtering
UTM Firewall & Web Filtering
 High Speed IPS
High Speed IPS
 Blocks Ransomware / Malware
Blocks Ransomware / Malware
 Block 600+ million bad IPs
Block 600+ million bad IPs
- UTM 64 Bit Firewall.
- Anti Spam & Anti Virus.
- Web Filter & Content Filter.
- IPS - VPN, Wireguard VPN.
- Block Torrent TOR, Control Social Media.
SecPoint® Protector™ 1U Rack Appliance Click here
SecPoint® Cloud Penetrator™ - Web Vulnerability Scanner
 Web Application Scanning
Web Application Scanning
 SQL Injection - Cross Site Scripting
SQL Injection - Cross Site Scripting
 Web Vulnerability Scan
Web Vulnerability Scan
 Advanced AI Accurate scans
Advanced AI Accurate scans
- SSL Vulnerability Scanner
- Find popular SSL Vulnerabilities in your Site easily
- Heartbleed (CVE-2014-0160)
- CCS (CVE-2014-0224)
- BEAST (CVE-2011-3389)
- LUCKY13 (CVE-2013-0169)
- BREACH (CVE-2013-3587)
- POODLE, SSL (CVE-2014-3566)
- SWEET32 (CVE-2016-2183, CVE-2016-6329)
- FREAK (CVE-2015-0204)
- Ticketbleed (CVE-2016-9244)
- DROWN (CVE-2016-0800, CVE-2016-0703)
- And many more SSL checks.
- Web Security Scanning.
- CMS Joomla, Drupal, Wordpress Scanning.
- SQL Injection Scanning.
- XSS Cross Site Scripting Scanning.
- Automatic Notification of Vulnerabilities.
SecPoint® Portable Penetrator™ - WiFI Penetration Testing Software for password Recovery
 Recover WiFi Password
Recover WiFi Password
 WiFi Penetration Testing
WiFi Penetration Testing
 WPA2 - WPA - WPS WiFi Keys
WPA2 - WPA - WPS WiFi Keys
 Secure your WiFi Networks
Secure your WiFi Networks
- WPA/WPA2 Handshake Capture.
- WEP WPA WPA WPS Password Recovery.
- 1.1 Billion Entries for Cracking
- 30+ Languages Specific Word Lists Included
- 2.4 GHz and 5.8 GHz Supported.