SecPoint
SecPoint Penetrator S9 - 512 IP Concurrent Scan License Vulnerability Scanner (3 Years License)
SecPoint Penetrator S9 - 512 IP Concurrent Scan License Vulnerability Scanner (3 Years License)
Regular price
€12.144,62 EUR
Regular price
Sale price
€12.144,62 EUR
Unit price
per
Tax included.
Shipping calculated at checkout.
Couldn't load pickup availability
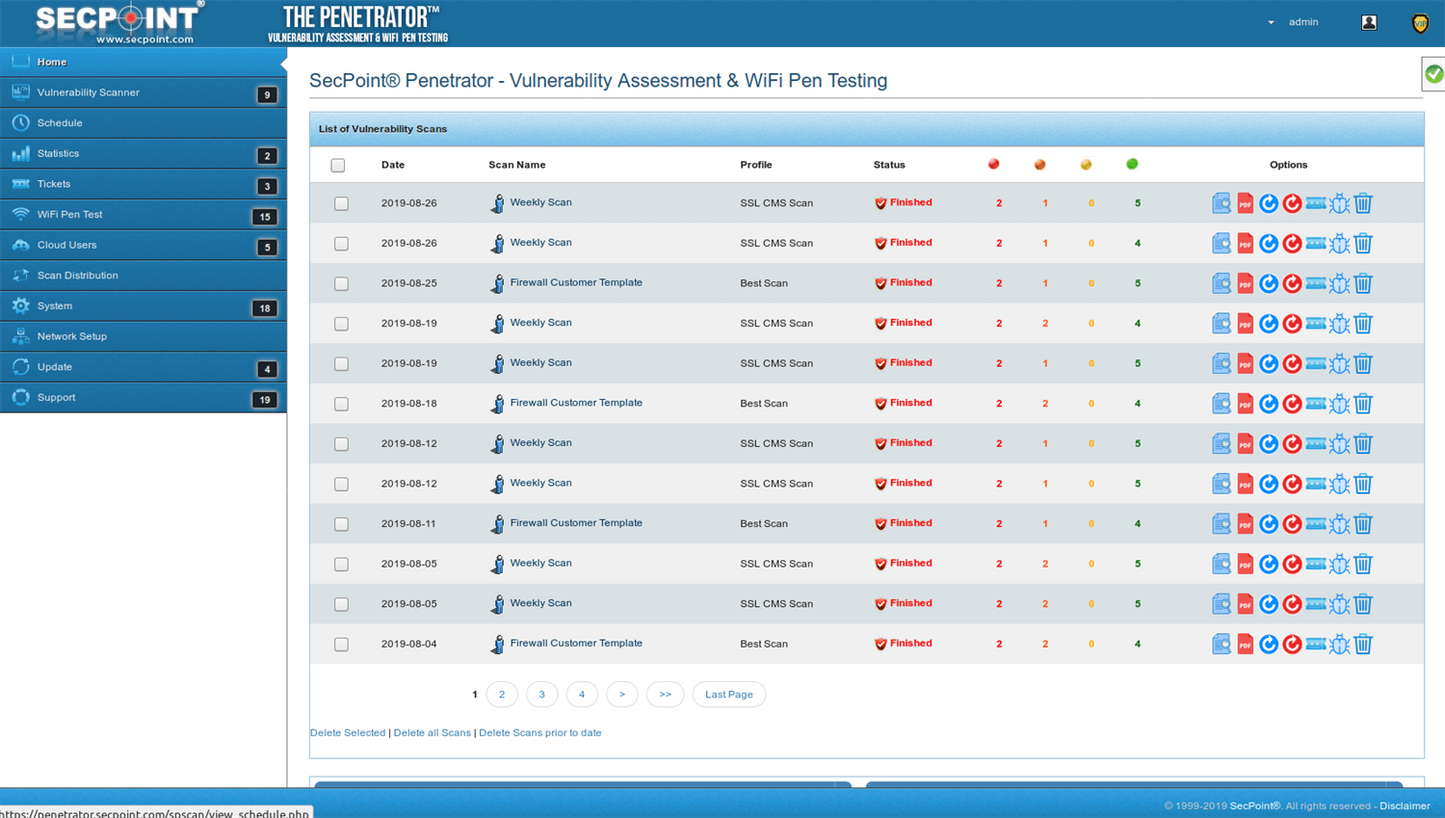
SecPoint® Penetrator™ key features:
- 143,000+ Vulnerability Checks
- 1,400+ Web Shells Detection
- Data Leak Detection
- Lethal Attack Technology
- Daily updated database
- 25 Report Languages
- 33 Vulnerability Scan Profiles
- Dark Web Search 4.0
- Easy to use GUI interface
- Advanced AI High Accuracy
- Easy scheduling of vulnerability scans
- Managed Service Provider (MSP)
- Whitelabeling
- Notification on email about scan status
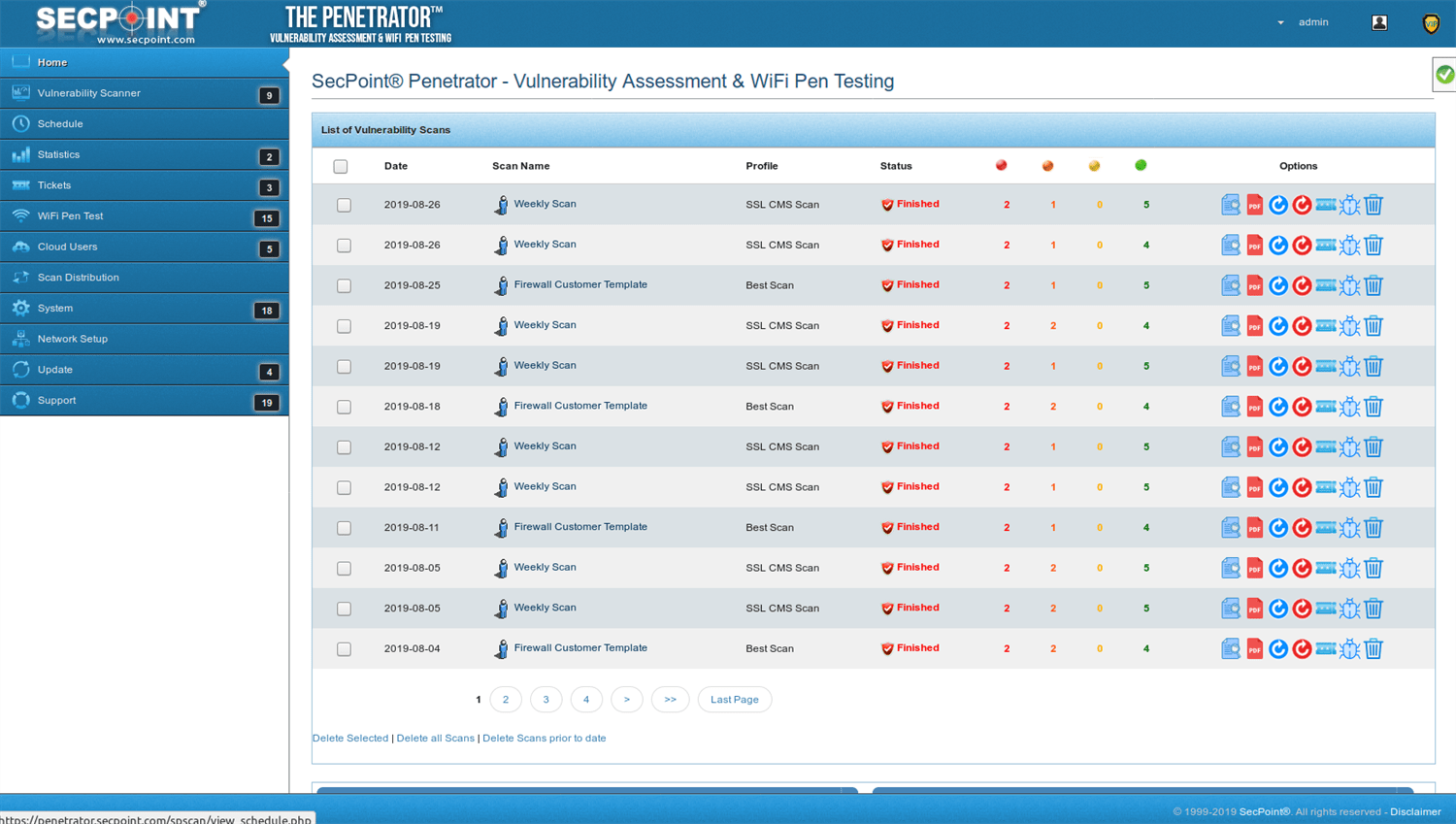
- Vulnerability Scanning & Assessment
- Scan local & public IPs
- SQL Injection, Blind SQL Injection
- Command Execution, Information Disclosure
- Cross Site Scripting (XSS)
- Reflected Cross Site Scripting
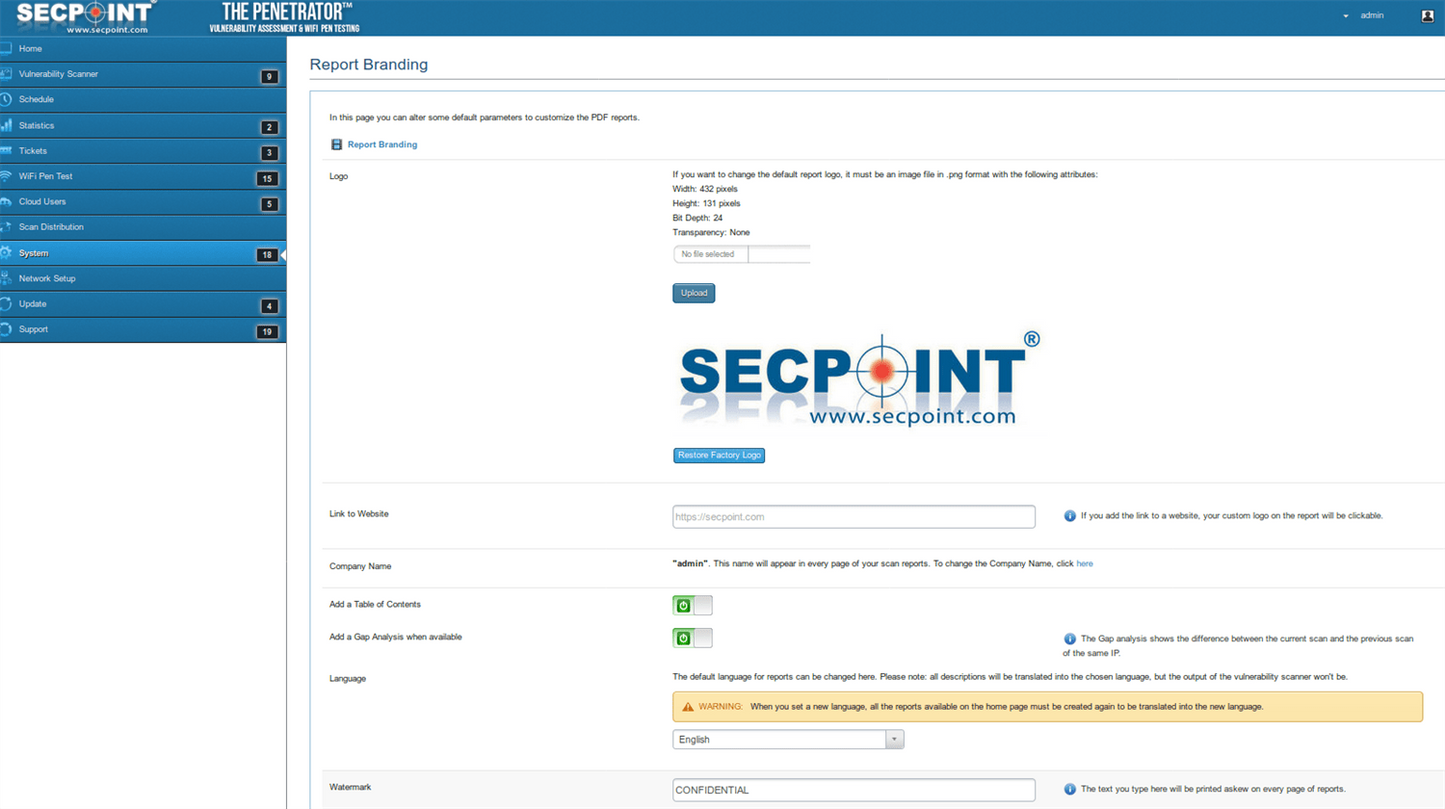
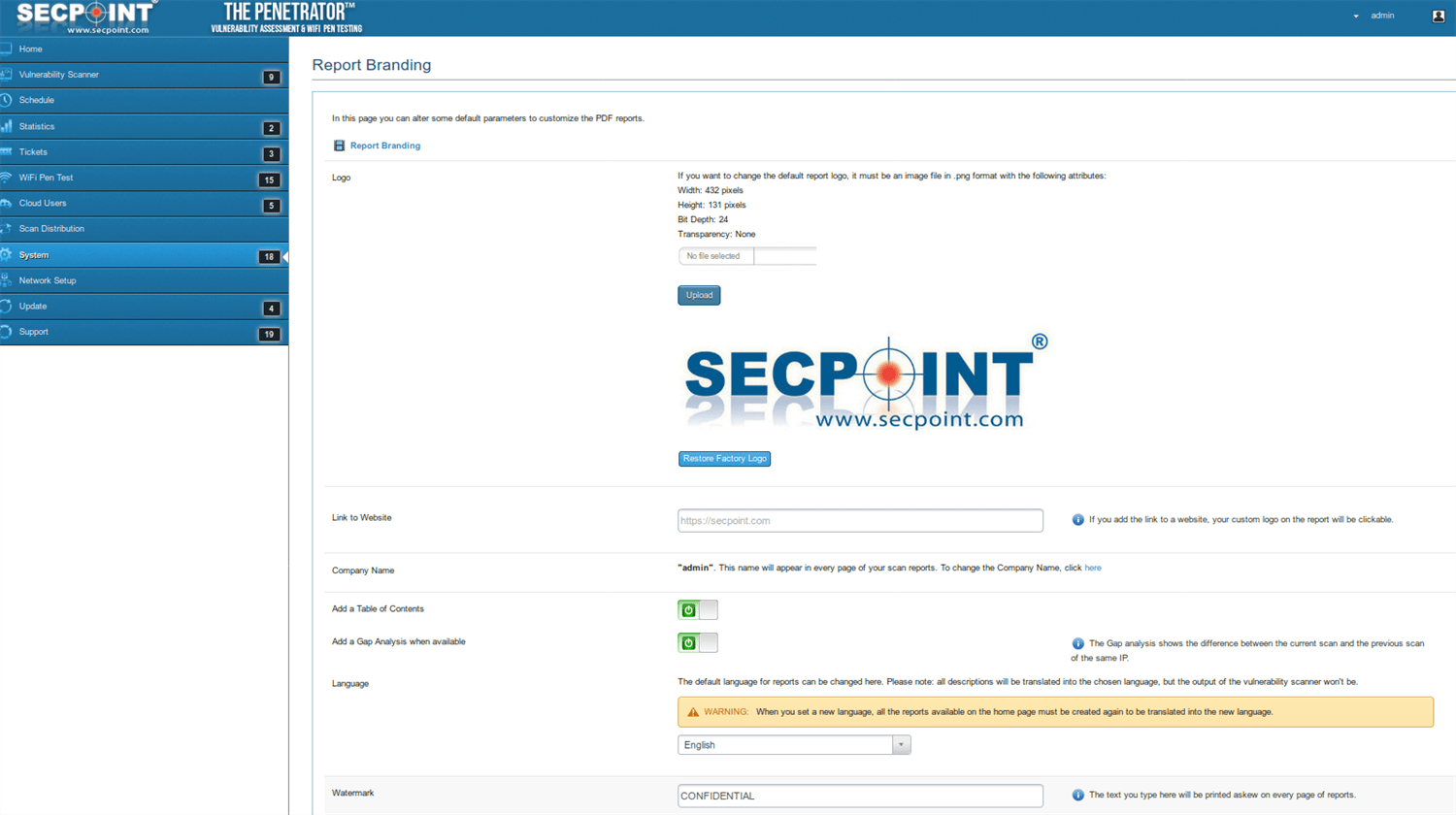
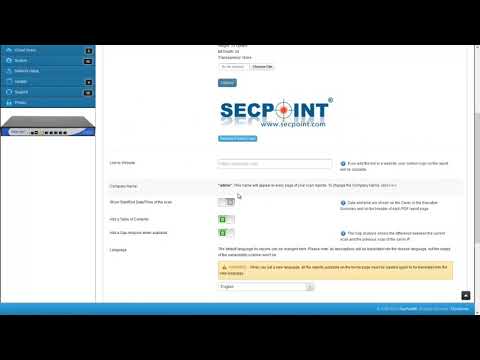
- Customize reporting with logo,name,watermark
- Notification by email when new vulnerabilities are discovered
- SecPoint® RBL List
- Block 640+ Million Toxic IPs
- SCADA & IoT UPC: 633710371315 EAN: 0633710371315
Professional Vulnerability Scanning and Assessment Software Suite
Vulnerability Scanning , Pen Testing, Vulnerability Assessment Perfect as a consultant edition. Customize reporting with watermark, logo, name. Supported platforms: VMware Player/Workstation, ESXi, Hyper-V or Raw Linux ISO.SecPoint® Penetrator™ Virtual Software Appliance
Vulnerability Scanning - Cross Site Scripting, XSS, SQL Injection, Vulnerability assessmentBrowse your web servers for vulnerabilities.
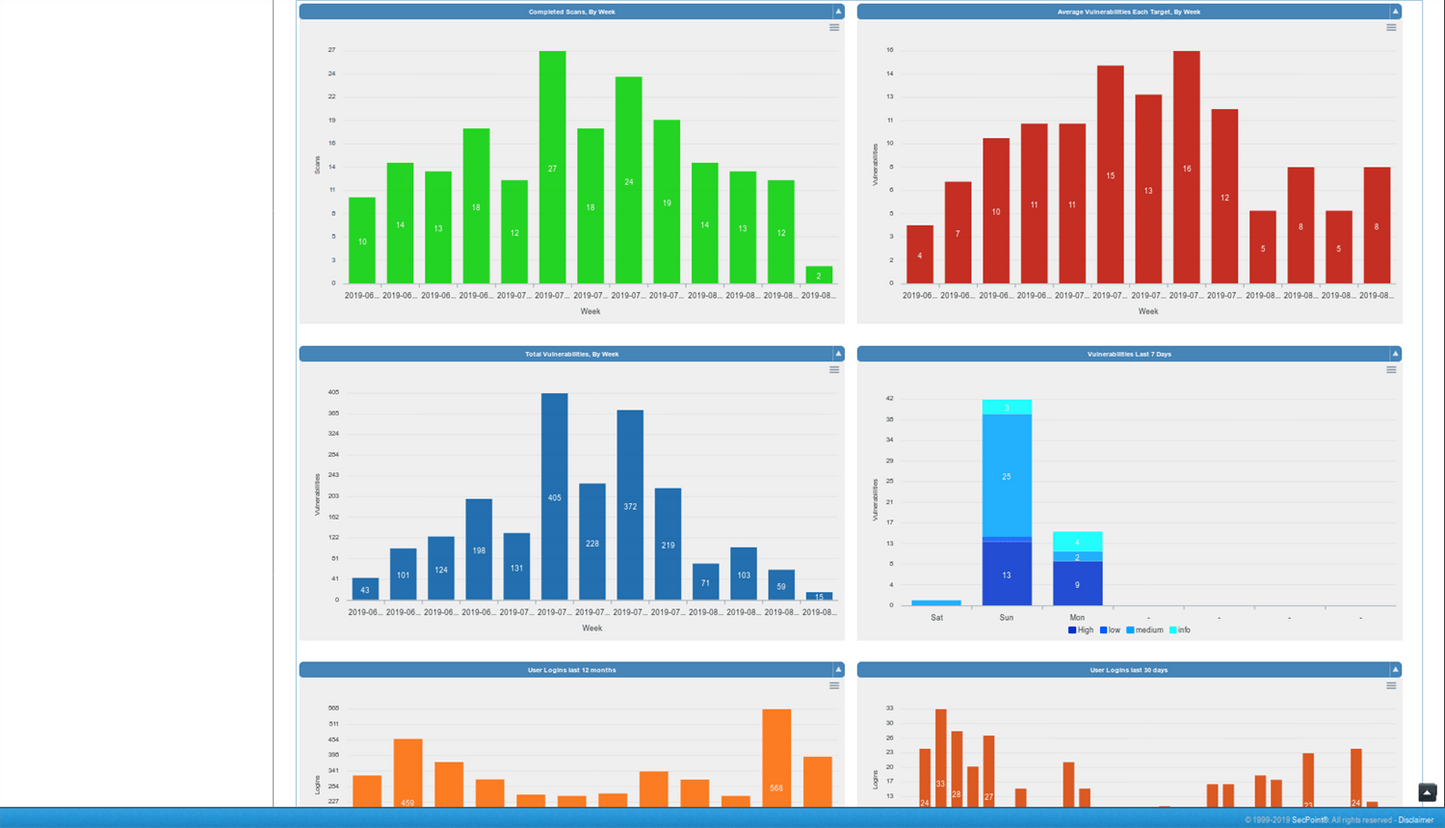
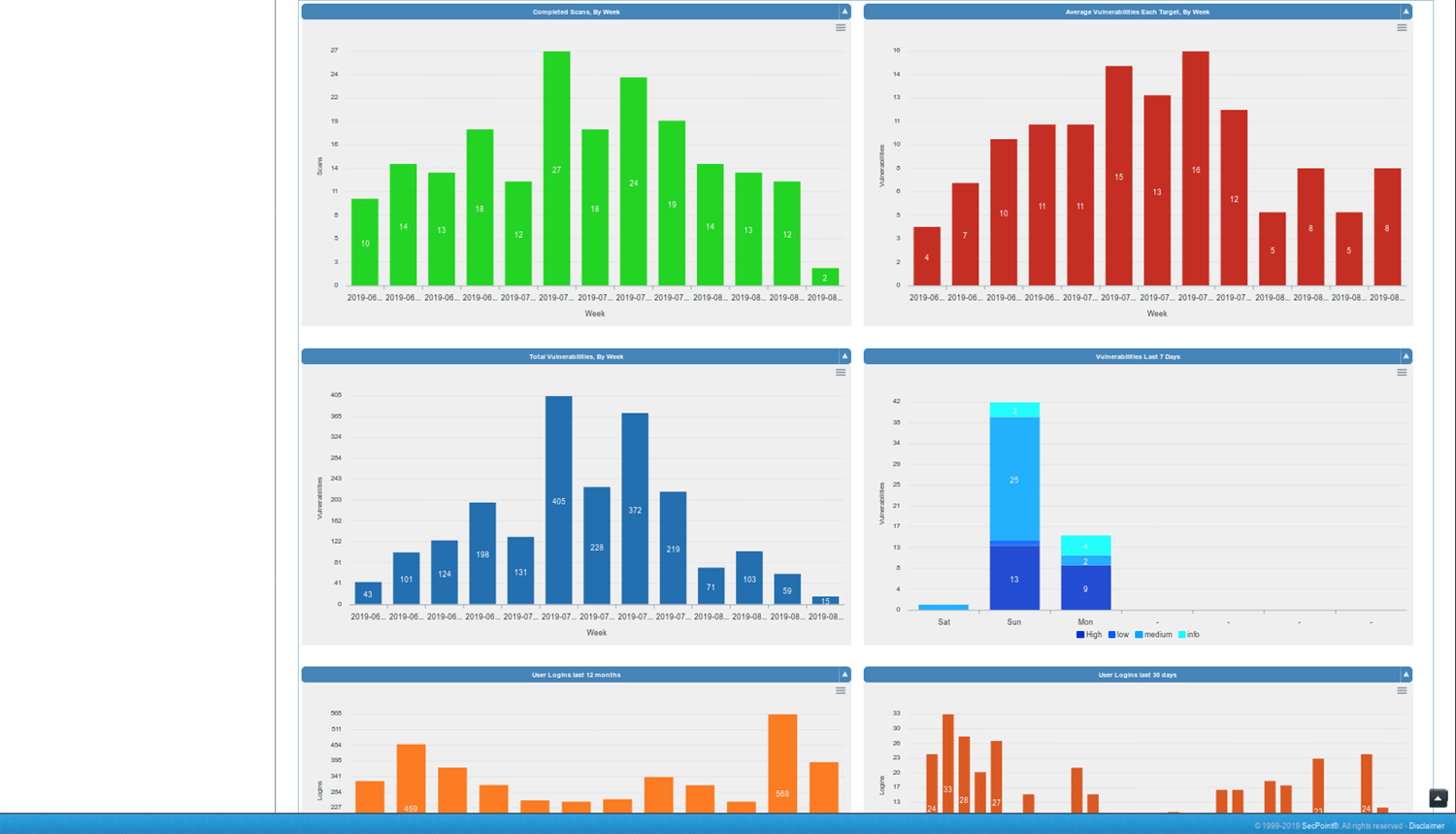
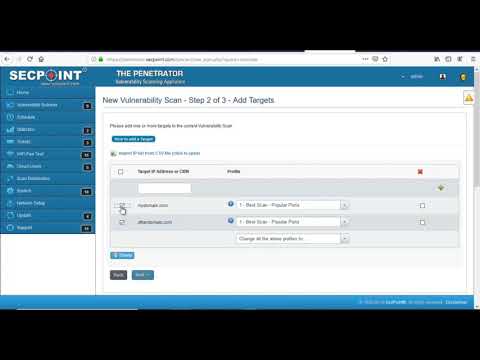
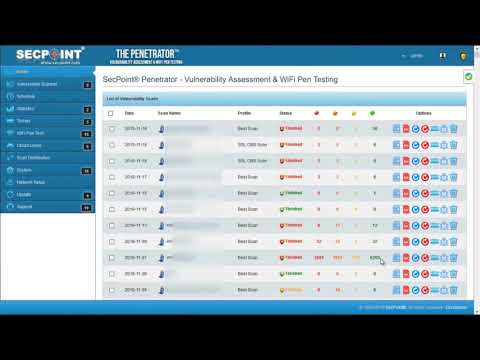
Easy to use interface GUI operate with no experience. Scan internal and public IP addresses for vulnerabilities. WiFi Adapter not included. Must be purchased separately for WiFi Pen testing functionality. Rebrand the PDF report and upload your own logo, watermark text and company name. Automatic schedule scanning that will notify you of new vulnerabilities. Easy to use help desk system so you can keep track of vulnerabilities and to close them. Advanced profiles for scanning. More than 30 advanced scanning profiles including Firewall evasion scanning, Aggressive Profiles and more. Easily create tickets to manage the fixing of vulnerabilities. Statistics and trends allows to show the history of vulnerability scans. False positive system to easily downgrade vulnerabilities or remove them from reports. SecPoint® Penetrator™ complete vulnerability scanning, penetration testing. SecPoint® Penetrator™ Vulnerability Scanning Software! We live in a world where the internet is the most important aspect of our life and we are extremely protective about it. One moment the speed goes wrong, the other moment we are wallowing in despair for being unable to access the e-mail or maybe do something else on the internet. There are hackers present everywhere who are lurking around every corner just waiting to attack your network. That is why it is very important for you to ensure that you keep it protected and all loop holes are fulfilled as well. This type of software must be easy to use so that even a normal individual can take advantage of it. You can now discover the various vulnerabilities present in Firewalls, IPs and Routers along with Windows and printers. Your mobiles can also be protected using this software. The main point to retain in mind is that every device is important and the data it carries is also highly important. You must therefore, put this software to its best use. This software can easily be deployed in your network and then vulnerability management can then be conveniently carried out. Local IP addresses and public ones can be scanned too very easily. The report will be presented to you in detail in PDF or HTML. Clear solutions will be presented to you so that you can easily deal with the issue at hand and get rid of the problem. Scheduling can be set up easily as well and this can also lead to you getting notifications about any vulnerability that gets discovered. Avoid compromising your network! There is a series of weak points that can be dealt with: - The vulnerabilities could be found and then these areas could be strengthened.
- The design could be secured.
- The interaction is not remote at all.
- Solutions are granted that can help the problems to be easily coped with.
- The solutions are also very clear.
- The security of the application is very amazing.
- These software are usually very user friendly and can be installed very easily. There are software packages which have amazing feature set. There is also a scanning engine includes many options for scanning which have been pre-defined. These include a normal scan, extended scan and firewall scan. Reports are generated and can be easily viewed as well. The software also comes ready for WiFi encryption. Most software also have a customer service available a live chat support is there to allow you attain the aid you are in need of. There is also assistance areas on the internet which includes product documentation and this is very well organized. It can also be followed very easily and screen shots and instances are also available. Here are some prime features which must be kept in mind at all times:
- PDF Reporting is present
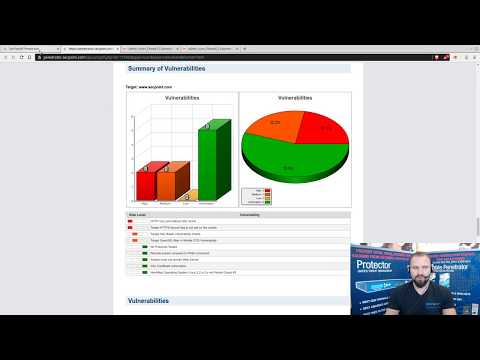
- Launch DoS is also available SecPoint® Penetrator™ Virtual Software Appliance SecPoint® Penetrator™ Best Cyber Security Vulnerability Scanner can help you to scan all your internal and external IP addresses for vulnerabilities. You will get clear evidence of found vulnerabilities and solutions how to resolve the found vulnerabilities. You can easily rescan to confirm the vulnerabilities are fixed. It has powerful scanning engine with daily updates. SecPoint® Penetrator™ Brochure
SecPoint® Penetrator™ Datasheet SecPoint® Penetrator™ Output Example Report SecPoint® Penetrator™ Executive Report